SRTP
SRTP: Secure Real-time Transport Protocol
SRTP is a security profile for RTP that adds confidentiality, message authentication, and replay protection to that protocol. SRTP is ideal for protecting Voice over IP traffic because it has no effect on voice quality and payload overhead is only minimally affected.
Secure variants include support for:
Authentication Algorithm Types: HMAC-SHA1 and MD5
Key Definition Schemes: PSK, MKI, and FT
Features List
- Encryption Algorithm Types: AES – CM, AES – F8
- Supports multiple SRTP and SRCTP streams with same or different peers simultaneously
- Master key used to derive session keysza
- SRTP (Secure RTP ) conform to IETF RFC 3711
- eXpressDSP™ Algorithm Interoperability Standard (xDIAS) Compliant
TERMINOLOGY
RTP – Real-time Transport Protocol
SRTP – Secure Real-time Transport Protocol
AES – Advanced Encryption Standard
AES CM – Advanced Encryption Standard counter mode
AES-f8 – AES in f8-mode, Universal Mobile Telecommunications System (UMTS) 3G mobile networks
use AES-f8.
Authentication Algorithm HMAC – Hashed message authentication code is characteristically used to authenticate that a message has not been changed during transit. Both parties to the message must have a shared secret key. The sender combines the key and the message into a string, produces a digest of the string by using an algorithm such as SHA-1 or MD5, and transmits the message and the digest. The receiver joins the shared key with the message, applies the appropriate algorithm, and runs a comparison between the digest thus obtained with that transmitted by the sender. If the digests are precisely the same, the message has not been tampered with.
Authentication Algorithm MD5 – Message Digest 5 is a widely used cryptographic hash function with a 128-bit hash value. As an Internet standard (RFC 1321), MD5 has been employed in a wide variety of security applications, and is also commonly used to check the integrity of files.
MKI – Master key identifier
Availability
| Platforms |
| Arm ® Devices – Cortex-A8 / A9 / A15 || Legacy ARM9E/ARM11 |
| Texas Instruments – TI TMS320C6000 C64x/C64x+/C66x, C674x, C62/C67 | TMS320C5000 C55x, C54x |
ADT SRTP is available on the above Platforms: Other configurations are available upon request.
Specifications
NOTE: We specify MIPS (Millions of Instructions Per Second) as MCPS (Millions of Instruction Cycles Per Second). Unless otherwise specified, peak MIPS are indicated.
↓ Click on links below to view specification tables.
Note: All CPU usage given in MIPS (also known as MCPS or MHz)
ARM Cortex-A8/A9/A15/A17
CPU UTILIZATION| Payload Size | Frame Rate | 10 | 20 | 30 |
| (Bytes/10 msec) | (msec) | Avg | Avg | Avg |
| 10 | Encrypt | 0.6 | 1.1 | 1.2 |
| Decrypt | 0.9 | 1.1 | 1.1 | |
| Encrypt + Auth | 13 | 1.8 | 1.8 | |
| Decrypt + Auth | 1.3 | 1.8 | 1.8 | |
| 80 | Encrypt | 2.6 | 5.1 | 7.6 |
| Decrypt | 2.6 | 5.2 | 7.6 | |
| Encrypt + Auth | 3.6 | 6.1 | 8.8 | |
| Decrypt + Auth | 3.5 | 6.1 | 8.9 |
MEMORY REQUIREMENTS
All Memory usage is given in units of byte.
| Memory Type | Usage | Alignment |
| Shared Program | 45264 | N/A |
| Shared Data | 2240 | N/A |
| Per-Thread Scratch | 320 | N/A |
| Per-Channel Context Send | 840 | 8 byte |
| Per-Channel Context Receive | 864 | 8 byte |
SRTP ARM9E / ARM11
CPU UTILIZATION| Payload Size | Frame Rate | 10 | 20 | 30 |
| (Bytes/10 msec) | (msec) | Avg | Avg | Avg |
| 10 | Encrypt | 0.6 | 1.2 | 1.1 |
| Decrypt | 0.7 | 1.1 | 1.1 | |
| Encrypt + Auth | 1.2 | 1.7 | 1.7 | |
| Decrypt + Auth | 1.3 | 1.6 | 1.7 | |
| 80 | Encrypt | 2.5 | 5 | 7.4 |
| Decrypt | 2.7 | 5 | 7.4 | |
| Encrypt + Auth | 3.3 | 5.8 | 8.5 | |
| Decrypt + Auth | 3.3 | 5.8 | 8.5 |
MEMORY REQUIREMENTS
All Memory usage is given in units of byte.
| Memory Type | Usage | Alignment |
| Shared Program | 43292 | N/A |
| Shared Data | 2192 | N/A |
| Per-Thread Scratch | 320 | N/A |
| Per-Channel Context Send | 840 | 8 byte |
| Per-Channel Context Receive | 864 | 8 byte |
TI TMS320C6000
Note: All CPU usage given in MIPS (also known as MCPS or MHz)
SRTP C64x+ / C66x / C674x
CPU UTILIZATION| Payload Size (Bytes/10 msec) | Frame Rate (msec) | 10 Avg | 10 Peak | 20 Avg | 20 Peak | 30 Avg | 30 Peak |
| 10 | Encrypt | 0.31 | 1.75 | 0.29 | 0.99 | 0.19 | 0.67 |
| Decrypt | .32 | 1.75 | 0.29 | 1 | 0.2 | 0.67 | |
| Encrypt + Auth | .97 | 2.41 | 0.61 | 1.32 | 0.42 | 0.89 | |
| Decrypt + Auth | 0.98 | 2.4 | 0.62 | 1.33 | 0.42 | 0.89 | |
| 80 | Encrypt | 1.36 | 2.78 | 1.34 | 2.05 | 1.33 | 1.81 |
| Decrypt | 1.38 | 2.8 | 1.35 | 2.06 | 1.34 | 1.81 | |
| Encrypt + Auth | 2.16 | 3.58 | 1.81 | 2.52 | 1.73 | 2.2 | |
| Decrypt + Auth | 2.18 | 3.59 | 1.82 | 2.52 | 1.74 | 2.21 |
MEMORY REQUIREMENTS
All Memory usage is given in units of byte.
| Memory Type | Usage | Alignment |
| Shared Program | 32,00 | N/A |
| Shared Data | 870 | N/A |
| Per-Thread Scratch | 320 | N/A |
| Per-Channel Context Send | 840 | 8 byte |
| Per-Channel Context Receive | 864 | 8 byte |
SRTP C64x
CPU UTILIZATION| Payload Size (Bytes/10 msec) | Frame Rate (msec) | 10 Avg | 10 Peak | 20 Avg | 20 Peak | 30 Avg | 30 Peak |
| 10 | Encrypt | 0.33 | 1.82 | 0.3 | .1.04 | 0.2 | 0.7 |
| Decrypt | .34 | 1.80 | 0.3 | 1.03 | 0.21 | 0.69 | |
| Encrypt + Auth | .99 | 2.48 | 0.63 | 1.37 | 0.42 | 0.92 | |
| Decrypt + Auth | 1 | 2.46 | 0.64 | 1.36 | 0.43 | 0.91 | |
| 80 | Encrypt | 1.38 | 2.87 | 1.35 | 2.09 | 1.34 | 1.83 |
| Decrypt | 1.4 | 2.85 | 1.36 | 2.1 | 1.34 | 1.83 | |
| Encrypt + Auth | 2.18 | 3.66 | 1.82 | 2.56 | 1.74 | 2.23 | |
| Decrypt + Auth | 2.2 | 3.65 | 1.83 | 2.55 | 1.75 | 2.23 |
MEMORY REQUIREMENTS
All Memory usage is given in units of byte.
| Memory Type | Usage | Alignment |
| Shared Program | 38200 | N/A |
| Shared Data | 870 | N/A |
| Per-Thread Scratch | 320 | N/A |
| Per-Channel Context Send | 840 | 8 byte |
| Per-Channel Context Receive | 864 | 8 byte |
TI TMS320C5000
SRTP C55x
CPU UTILIZATION| Payload Size (Bytes/10 msec) | Frame Rate (msec) | 10 Avg | 10 Peak | 20 Avg | 20 Peak | 30 Avg | 30 Peak |
| 10 | Encrypt | 2.98 | 15.57 | 2.94 | 9.22 | 1.96 | 6.15 |
| Decrypt | 3 | 15.59 | 2.95 | 9.23 | 1.97 | 6.15 | |
| Encrypt + Auth | 4.17 | 16.76 | 3.54 | 9.81 | 2.36 | 6.54 | |
| Decrypt + Auth | 4.2 | 16.62 | 3.55 | 9.83 | 2.37 | 6.55 | |
| 80 | Encrypt | 14.58 | 27.24 | 14.54 | 20.81 | 14.53 | 18.66 |
| Decrypt | 14.6 | 27.09 | 14.55 | 20.82 | 14.54 | 18.73 | |
| Encrypt + Auth | 16.04 | 28.51 | 15.4 | 21.66 | 15.27 | 19.45 | |
| Decrypt + Auth | 16.07 | 28.71 | 15.4 | 21.67 | 15.28 | 19.46 |
MEMORY REQUIREMENTS
All Memory usage is given in units of byte.
| Memory Type | Usage | Alignment |
| Shared Program | 16677 | N/A |
| Shared Data | 1696 | N/A |
| Per-Thread Scratch | 320 | N/A |
| Per-Channel Context Send | 1300 | 8 byte |
| Per-Channel Context Receive | 1324 | 8 byte |
Description
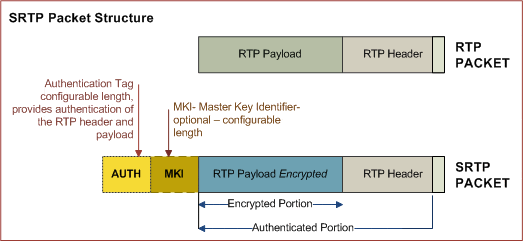
SRTP, & SRTCP are not separate protocols but are profiles of RTP. When security is being used, the packet payloads are encrypted.
RTP is specifically designed to handle the play-out requirements of real-time media streams through the use of time stamps and jitter buffering. Due to the real-time nature of the data streams, where requesting retransmissions is too costly in time, RTP is typically used in conjunction with UDP to provide low-overhead network communications between two end-points.
RFC 3550 identifies two components to the real-time transport: data transport and control. Data transport is handled by RTP while control is handled by Real Time Control Protocol (RTCP). RTCP, which can be used to help scale the network traffic to the available bandwidth, is optional.
An RTP packet identifies the media payload type (format) and its source. It also includes time stamps and sequence numbers that are used by the play-out side to handle lost or out of sequence packets. RTP provides for the use of multiple streams as in the case of a system that transmits both voice and video. The payload in an RTP payload contains the encoded voice or video information. The use of dynamically defined payload types allows RTP packets to carry virtually any type of media format.
* Adaptive Digital currently does not support RTCP.